Body:
ADFS – Active Directory Federation Service – STEP by STEP installation for O365
A main tool for corporate network to maintain on-prem and cloud-prem on a single sign-on environment. Deployment of ADFS is always happening on-prem and will sync to the cloud to maintain the AD structure and security through..secure tunnel
Office 365 – cloud configuration – Live ADFS or Active directory Federation Service is to deploy a new AD FS 2.0 infrastructure to provide your Active Directory users, who are logged on to computers located physically on the corporate network or that are logged on remotely to the corporate network, with single sign-on access to Office 365 services using their corporate domain credentials. Once you have deployed your AD FS 2.0 production environment on-premises, you will need to establish a relying party trust relationship between the AD FS 2.0 federation server farm and Office 365. This relying party trust acts as a secure channel where authentication tokens can safely pass between your organization and Office 365 in order to facilitate single sign-on access to Office 365.
AD FS 2.0 supports software virtualization of both the federation server and federation server proxy roles…Certificates play the most critical role in securing communications between federation servers, federation server proxies, Office 365, and web clients. The requirements for certificates vary, depending on whether you are setting up a federation server or a federation server proxy.
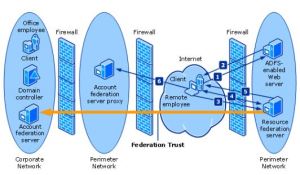
ADFS Architecture
The core architecture of Active Directory Federation Services (ADFS) requires an Active Directory (AD) or Active Directory Application Mode (ADAM) instance that contains user credentials. ADFS doesn’t replace the existing account repository; rather, it extends the repository’s visibility to other organizations in a highly controller manner. ADFS is a security token service that’s used mainly to compile statements about the user account in the form of security tokens, For custom applications, ADFS also populates claims, which are statements about the security principal (e.g., username, user’s title), that the Web application uses to ascertain the level of access that should be given to the requesting user. ADFS also manages the federation trusts it shares with other organizations’ federated services. A federation trust isn’t an AD forest trust; rather, it’s a special trust that uses certificates for token signing between organizations. The trusting forest can’t use the federation trust to query information about accounts in the account forest. The only information the trust ever sees is when specific users attempt to access Web services in its forest, and then it sees only account information designated as appropriate for that relationship. Federated-services servers in different organizations never communicate with each other; all communication occurs via the requesting client, which means the ports that have to be open for a typical domain trust aren’t required for a federated trust. Creation of the federated trust is all done out-of-band with only the signing certificate for the account side of the trust required at both ends, which can be sent via an email or burned to media and sent via carrier. All communication from the client is via HTTP Secure (HTTPS, port 443).
I’m gonna talk more from the real time scenario of
- How to do a single co-existence or mixed co-existence.
- Deployment of O365 environment.
- Planning O365.
- Migration platform.
- De-commissioning process.
- License model.
Single sign-on:
Single sign-on, also called identity federation, allows you and your users to access services in Microsoft Office 365 for enterprises with your Active Directory corporate credentials. Without single sign-on, you, the administrator, and your users will need to maintain separate user names and passwords for your online and on-premises accounts. Single sign-on requires both Active Directory Federation Services (AD FS) 2.0 and Active Directory synchronization. When you set up single sign-on, you establish a relying party trust between AD FS 2.0 and Office 365. Local Active Directory users obtain authentication tokens from AD FS 2.0 that redirect the users’ requests through the relying party trust. This allows your users to access Office 365 without needing to sign in with different credentials.
- Have Active Directory deployed and running in Windows Server 2003 operating system, Windows Server 2008, or Windows Server 2008 R2 with a functional level of mixed or native mode.
- Plan for and deploy AD FS 2.0 on Windows Server 2008 or Windows Server 2008 R2. Also, if the user is connecting from outside your company’s network, you must deploy an AD FS 2.0 proxy.
- Use the Microsoft Online Services Module for Windows PowerShell to establish a trust with Office 365.
- Install the required updates for Office 365 from the Office 365 downloads page to ensure that your users are running the latest updates of either Windows 7, Windows Vista, or Windows XP. To access the Office 365 downloads page, sign in to the Office 365 portal, and, under Resources, click Downloads. The features in Office 365 will not work properly without the appropriate versions of operating systems, browsers, and software.
AD FS 2.0 deployment
AD FS 2.0 supports software virtualization of both the federation server and federation server proxy roles.
AD FS 2.0 deployment to create a relying party trust successfully with Office 365, you must first make sure that your corporate network infrastructure is configured to support AD FS 2.0 requirements for accounts, name resolution, and certificates. AD FS 2.0 has the following types of requirements:
- Software requirements.
- Certificate requirements.
- Network requirements.
Software requirements
AD FS 2.0 software must be installed on any computer that you are preparing for the federation server or federation server proxy role. You can install this software by either using the AD FS 2.0 Setup Wizard or by performing a quiet installation using the adfssetup.exe /quiet parameter at a command line.
Installation platform: Windows Server 2008 or Windows Server 2008 R2.
Prerequisites:
During the AD FS 2.0 installation process, the setup wizard attempts to automatically check for and, if necessary, install both prerequisite applications and dependent hotfixes. In most cases the setup wizard will install all of the prerequisite applications necessary for AD FS 2.0 to operate and install. However, when you are installing AD FS 2.0 on the Windows Server 2008 platform. you will first need to make sure that .NET 3.5 SP1 is installed on the servers running Windows Server 2008 before installing the AD FS 2.0 software, as it is a prerequisite of AD FS 2.0 and it will not automatically be installed.
Hotfixes:
You must install AD FS 2.0 hotfixes after you have installed AD FS 2.0. Click here to download the hotfixes
Certificate requirements:
For securing communications between federation servers, federation server proxies, Office 365, and web clients. AD FS 2.0 requires an SSL certificate when configuring federation server settings. This is a standard Secure Sockets Layer (SSL) certificate that is used for securing communications between federation servers, clients, and federation server proxy computers. Please note that AD FS 2.0 requires this SSL certificate to be without a dotless (short-name) Subject name. Because this certificate must be trusted by clients of AD FS 2.0, use an SSL certificate that is issued by a public (third-party) CA or by a CA that is subordinate to a publicly trusted root.
Certificate Providers (Please make sure that all digital certificates expiring after December 31, 2013 request must have 2048-bit or greater key size…after December 31, 2012, 1024-bit keys will not be accepted for any certificates…click here to know more.)
Deploying ADFS Server – Farm. (For a standalone server, you just have to install on one of the server and publish it)
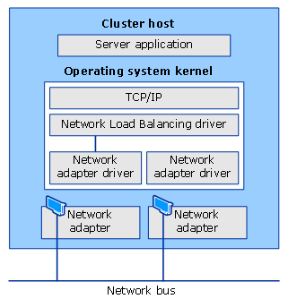
Why Farm ? When you host your email and SPS and Lync on the cloud/O365 and you have opt to go for a federated domain, your AD is sitting in your local network and users on the cloud needs to authenticate it. That is when the ADFS on a clustered/Farm is very important. Availability for this server is very important. For high availability, we need NLB (Network Load Balancing).
NLB provides many features that make it convenient to use:
- NLB is installed as a standard Windows networking driver component.
- NLB requires no hardware changes to enable and run.
- NLB Manager enables you to create new NLB clusters.
- NLB Manager enables you to configure and manage multiple clusters and all of the cluster’s hosts from a single remote or local computer.
Checklist for ADFS deployment.
- Prepare your ADFS network infrastructure(Here you can select where you want your server to be..Virtual/Physical, Network, IP etc)
- Install the machineusing Windows server 2008 R2.
- Join the computer to the domain.
- Install the second machine…and repeat step 2 and 3.
- Installing NLB feature on the server. To open the Add Features Wizard and install NLB
- Click Start, click Administrative Tools, and then click Server Manager.
- In the Features Summary area of the Server Manager main window, click Add Features.—or—In the Customize this server area of the Initial Configuration Tasks window, click Add Features.
- In the Add Features Wizard, select the Network Load Balancingcheck box.
- Click Install.
- Alternatively, you can install NLB by typing the following command: servermanagercmd.exe -install nlb.
- Create and configure a new NLB cluster (When you are using Network Load Balancing (NLB) Manager, you must be a member of the Administrators group on the host that you are configuring) – >To create a new NLB cluster (NOTE: NLB does not support Dynamic Host Configuration Protocol (DHCP). NLB disables DHCP on each interface that it configures, so the IP addresses must be static. )
- Open Network Load Balancing Manager, click Start, click Administrative Tools, and then click Network Load Balancing Manager. You can also open Network Load Balancing Manager by typing Nlbmgrat a command prompt.
- Right-click Network Load Balancing Clusters, and then click New Cluster.
- To connect to the host that is to be a part of the new cluster, in the Host text box, type the name of the host, and then click Connect.
- Select the interface that you want to use with the cluster, and then click Next. (The interface hosts the virtual IP address and receives the client traffic to load balance.)
- In Host Parameters, select a value in Priority (Unique host identifier). This parameter specifies a unique ID for each host. The host with the lowest numerical priority among the current members of the cluster handles all of the cluster’s network traffic that is not covered by a port rule.You can override these priorities or provide load balancing for specific ranges of ports by specifying rules on the Port rules tab of the Network Load Balancing Properties dialog box.In Host Parameters, you can also add dedicated IP addresses, if necessary.
- Click Next to continue.
- In Cluster IP Addresses, click Add and type the cluster IP address that is shared by every host in the cluster. NLB adds this IP address to the TCP/IP stack on the selected interface of all hosts that are chosen to be part of the cluster.
- Click Next to continue.In Cluster Parameters, select values in IP Address and Subnet mask (for IPv6 addresses, a subnet mask value is not needed). Type the full Internet name that users will use to access this NLB cluster.
- In Cluster operation mode, click Unicastto specify that a unicast media access control (MAC) address should be used for cluster operations. In unicast mode, the MAC address of the cluster is assigned to the network adapter of the computer, and the built-in MAC address of the network adapter is not used. We recommend that you accept the unicast default settings.
- Click Next to continue.
- In Port Rules, click Edit to modify the default port rules, if needed.
- To add more hosts to the cluster, right-click the new cluster, and then click Add Host to Cluster. Configure the host parameters (including host priority, dedicated IP addresses, and load weight) for the additional hosts by following the same instructions that you used to configure the initial host. Because you are adding hosts to an already configured cluster, all the cluster-wide parameters remain the same.
- Create DNS name. To add a resource record to corporate DNS for the cluster DNS name configured on the corporate NLB host
- On a DNS server for the corporate network, open the DNS snap-in.
- In the console tree, right-click the applicable forward lookup zone (for example, fabrikam.com), and then click New Host (A or AAAA).
- In Name, type only the computer name of the federation server or federation server cluster; for example, for the fully-qualified domain name (FQDN) fs.fabrikam.com, type fs.
- In IP address, type the IP address for the federation server or federation server cluster; for example, 172.16.1.3.
- Click Add Host.
- Generate a CSR from one of the ADFS serverand procure the SSL certificate that is issued by a public (third-party) CAertificate Authority for the NLB cluster name (here fs.fabrikam.com)
- Import the Certificate to the Default website on the ADFS (Please note that you have to install this certificate first on the CSR generating server). The server authentication certificate must match the FQDN of the cluster DNS name (for example, fs.fabrikam.com) you created earlier on the NLB host. If Internet Information Services (IIS) has not been installed, you must install IIS first in order to complete this task. To import a server authentication certificate to the Default Web Site
- Click Start, point to All Programs, point to Administrative Tools, and then click Internet Information Services (IIS) Manager.
- In the console tree, click ComputerName.
- In the center pane, double-click Server Certificates.
- In the Actions pane, click Import.
- In the Import Certificate dialog box, click the … button.
- Browse to the location of the pfx certificate file, highlight it, and then click Open.
- Type a password for the certificate, and then click OK.
- Create a dedicated service account for the federation server farm. You have to perform the tasks in this procedure only one time for the entire federation server farm. Later, when you create a federation server by using the AD FS 2.0 Federation Server Configuration Wizard, you must specify this same account on the Service Accountwizard page on each federation server in the farm. To configure a federation server farm environment in AD FS 2.0, you must create and configure a dedicated service account in Active Directory where the farm will reside. To create a dedicated service account for the federation server farm
- Create a dedicated user/service account in the Active Directory forest you will use in your organization.
- Edit the user account properties, and select the Password never expires check box. This action ensures that this service account’s function is not interrupted as a result of domain password change requirements. If you need to change your password for the service account on a regular basis, Click here.
- Install the AD FS 2.0 software and AD FS 2.0 hotfixeson the computers that will become federation servers.Locate the AdfsSetup.exe setup file that you downloaded to the computer, and then double-click it.
- On the Welcome to the AD FS 2.0 Setup Wizard page, click Next.
- On the End-User License Agreementpage, read the license terms.
- If you agree to the terms, select the I accept the terms in the License Agreement check box, and then click Next.
- On the Server Role page, select Federation server, and then click Next.
- On the Completed the AD FS 2.0 Setup Wizard page, click Finish.
- Install all of the hotfixesfor ADFS
- To create the first federation server in the AD federation server farm. After the AD FS 2.0 software installation is complete, click Start, then Administrative Tools, and then AD FS 2.0 Managementto open the AD FS 2.0 Management snap-in.
- On the Overview page, click AD FS 2.0 Federation Server Configuration Wizard.
- On the Welcome page, verify that Create a new Federation Service is selected, and then click Next.
- On the Select Stand-Alone or Farm Deployment page, click New federation server farm, and then click Next.
- On the Specify the Federation Service Name page, verify that the SSL certificate that is showing matches the name of the certificate that was imported into the Default Web Site in IIS previously. If this is not the correct certificate, select the appropriate certificate from the SSL certificate list.
- If you have previously reinstalled ADFS on this computer, then the Existing AD FS Configuration Database Detected page appears. If that page appears, click Delete database, and then click Next.
- On the Specify a Service Account page, click Browse. In the Browse dialog box, locate the domain account that will be used as the service account in this new federation server farm, and then click OK. Type the password for this account, confirm it, and then click Next.
- On the Ready to Apply Settings page, review the details. If the settings appear to be correct, click Next to begin configuring AD FS 2.0 with these settings.
- On the Configuration Results page, review the results. When all the configuration steps are finished, click Close to exit the wizard.
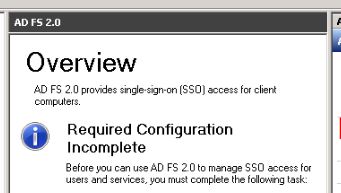
- When you finish the steps in this procedure, the AD FS 2.0 Management snap-in will automatically open and a message will appear indicating that the Required Configuration is Incomplete and that you should Add a trusted relying party.
- You can disregard this message. (The reason for this message to appear is that A relying party trust for Office 365 will be added in a later step. Once this step has been completed, this message will disappear from the AD FS 2.0 Management snap-in. )
- Add a federation server to the federation server farm. After the AD FS 2.0 software installation is complete, click Start, then Administrative Tools, and then AD FS 2.0 Management to open the AD FS 2.0 Management snap-in.
- On the Overview page, or in the Actions pane, click AD FS 2.0 Federation Server Configuration Wizard.
- On the Welcome page, verify that Add a federation server to an existing Federation Service is selected, and then click Next.
- If the AD FS 2.0 database that you selected already exists, the Existing AD FS Configuration Database Detected page appears. If that occurs, click Delete database, and then click Next.
- On the Specify the Primary Federation Server and Service Account page, under Primary federation server name, type the computer name of the primary federation server in the farm, and then click Browse. In the Browse dialog box, locate the domain account that is used as the service account by all other federation servers in the existing federation server farm, and then click OK. Type the password and confirm it, and then click Next.
- On the Ready to Apply Settings page, review the details. If the settings appear to be correct, click Next to begin configuring AD FS 2.0 with these settings.
- On the Configuration Results page, review the results. When all the configuration steps are finished, click Close to exit the wizard.
- Verify that the federation server is operational, Log on to a client computer that is located in the same forest as the federation server.
- Open a browser window. In the address bar, type the federation server’s DNS host name, and then append /FederationMetadata/2007-06/FederationMetadata.xml to it for the new federation server; for example: https://fs1.fabrikam.com/FederationMetadata/2007-06/FederationMetadata.xml
- Press ENTER, and then complete the next procedure on the federation server computer. If you see the message There is a problem with this website’s security certificate, click Continue to this website. The expected output is a display of XML with the service description document. If this page appears, IIS on the federation server is operational and serving pages successfully.
- Set up single sign-on is to download, install, and configure the Microsoft Online Services Module for Windows PowerShell. To know more, Click here.
- another